‘Identity Threat Detection and Response’ (ITDR)
With the increasing number of cyber threats and data breaches, individuals and organizations need to be proactive in detecting and responding to identity threats.
 Identity Threat Detection and Response is a proactive approach to safeguarding identities from cyber threats.
Identity Threat Detection and Response is a proactive approach to safeguarding identities from cyber threats.
It involves the use of advanced technologies and strategies to monitor, detect, and respond to potential threats that could compromise an individual’s or organization’s identity.
As Microsoft describes this emerging security focus area encompasses solutions designed to help prevent, detect, and respond to increasingly popular identity-related threats. Many identity attacks start when cybercriminals compromise credentials, typically through phishing or other social engineering strategies, but more recently sophisticated cyberattackers have begun targeting the underlying identity infrastructure to exploit vulnerabilities in identity posture.
Importance of Identity Threat Detection and Response
ITDR leverages advanced analytics, often powered by AI and machine learning, to identify suspicious activities related to identities and take immediate action to mitigate risks. Identity Threat Detection and Response is crucial for several reasons:
- Protecting sensitive information: By detecting and responding to identity threats, individuals and organizations can protect sensitive information such as personal data, financial details, and intellectual property.
- Preventing identity theft: Identity theft is a common cybercrime where attackers steal personal information to commit fraud. Identity Threat Detection and Response helps prevent such incidents.
- Ensuring regulatory compliance: Many industries have strict regulations regarding data protection. Implementing Identity Threat Detection and Response measures can help ensure compliance with these regulations.
- Preserving reputation: A data breach or identity theft incident can severely damage an individual’s or organization’s reputation. Identity Threat Detection and Response can help mitigate such risks.
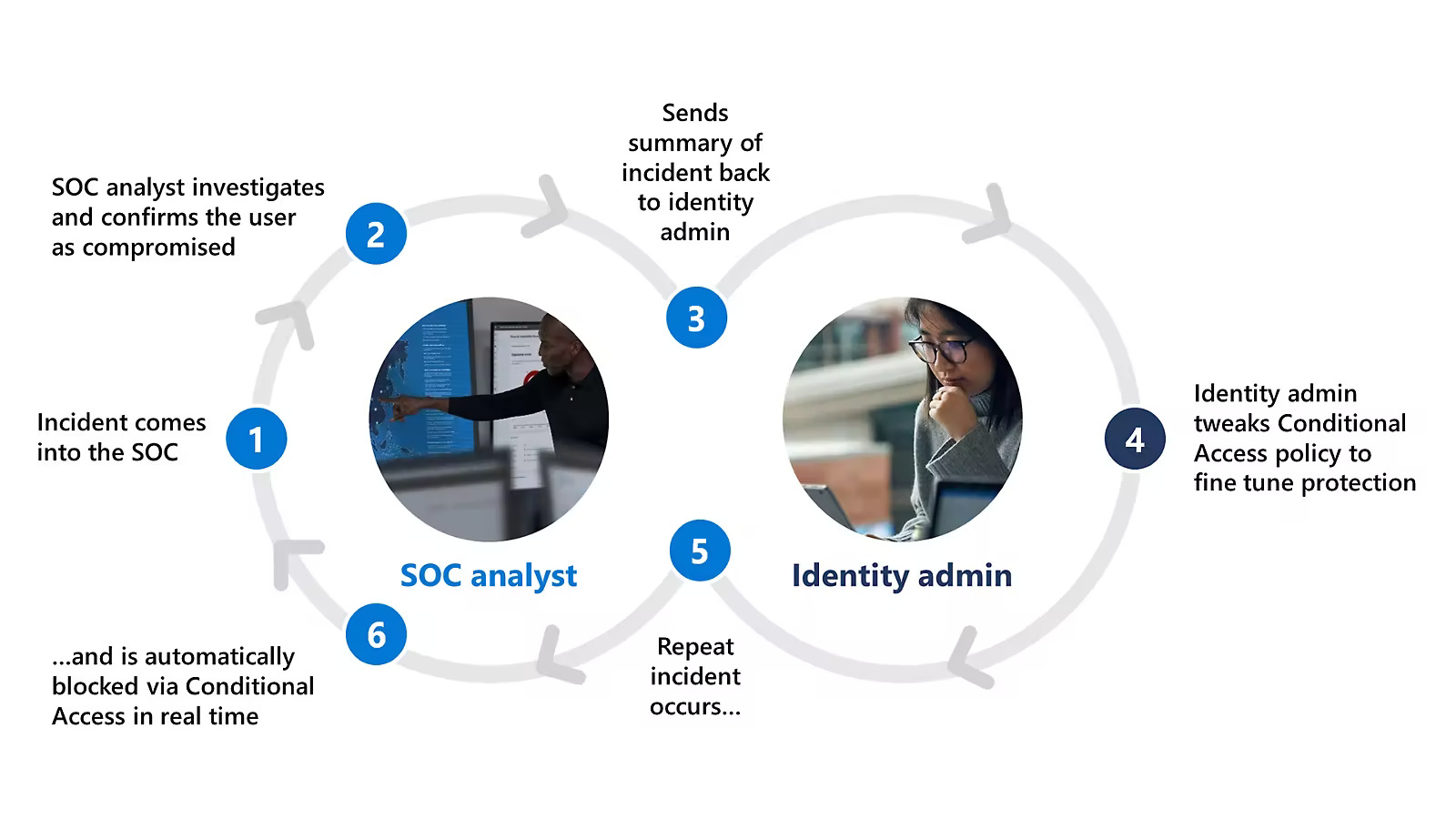
How does Identity Threat Detection and Response work?
ITDR monitors identity-related activities across systems, looking for anomalies such as unusual login patterns, privilege escalations, or access from unfamiliar locations or devices; it typically involves the following steps:
- Monitoring: Continuous monitoring of digital activities and networks to identify any suspicious behavior or anomalies.
- Detection: Using advanced algorithms and analytics to detect potential identity threats in real-time.
- Response: Implementing immediate response actions to mitigate the impact of identity threats and prevent further damage.
- Remediation: Conducting thorough investigations to understand the root cause of identity threats and implementing measures to prevent future incidents.
Identity Threat Detection and Response is a critical component of cybersecurity that helps individuals and organizations protect their identities from malicious actors. By implementing proactive measures and leveraging advanced technologies, identity threats can be detected and mitigated effectively, ensuring a safer digital environment for all.



