Respond Faster with an AI-powered Unified Security Operations Platform
Explore how Microsoft Security Copilot enhances the operational efficiency and effectiveness of your security operations center.
 Microsoft is deeply integrating artificial intelligence (AI), particularly generative AI, into its cybersecurity products to enhance threat detection, response, and overall security operations.
Microsoft is deeply integrating artificial intelligence (AI), particularly generative AI, into its cybersecurity products to enhance threat detection, response, and overall security operations.
This integration is transforming Security Operation Center (SOC) practices by automating tasks, improving efficiency, and addressing the global cybersecurity talent shortage.
Leveraging AI-powered tools like Microsoft Copilot for Security can significantly enhance an organization’s ability to detect, analyze, and respond to security incidents in real-time. Implementing an AI-powered Unified Security Operations Platform offers several key benefits:
- Enhanced threat detection capabilities
- Automated incident response processes
- Improved efficiency and accuracy in security operations
- Real-time monitoring and alerting
- Streamlined collaboration among security teams
Security Copilot
Launched in March 2023, Security Copilot is a generative AI-powered assistant that leverages large language models (LLMs) and Microsoft’s processing of 84 trillion daily signals to provide real-time threat analysis and response guidance. It integrates with Microsoft’s security suite, including Microsoft Sentinel, Defender, Purview, Entra, and Intune.
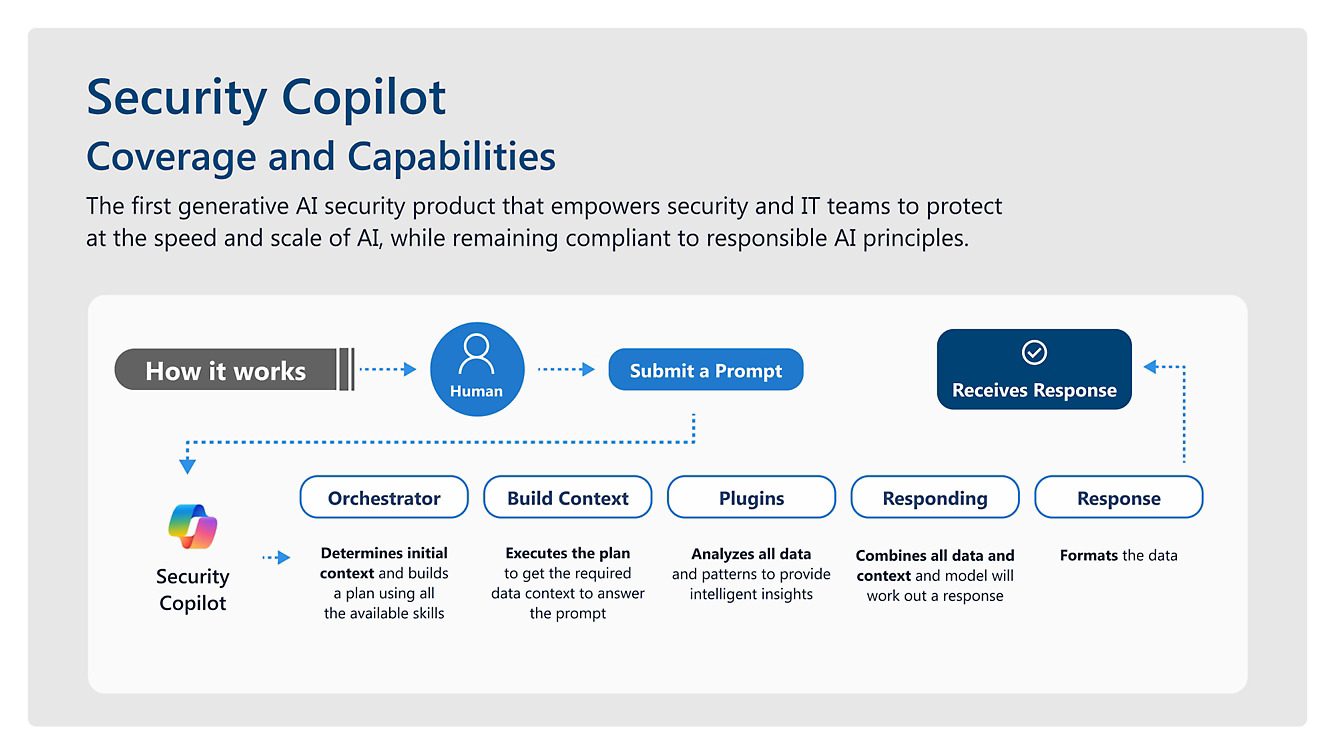
Key Features of Security Copilot
- Advanced Threat Detection: Security Copilot leverages AI and machine learning algorithms to identify and prioritize potential threats in real-time.
- Automated Response: The tool streamlines incident response processes by automating repetitive tasks and enabling faster remediation.
- Integration Capabilities: Security Copilot seamlessly integrates with existing security tools and platforms, providing a unified view of the organization’s security environment.
- Threat Intelligence Insights: By aggregating threat intelligence data, Security Copilot offers valuable insights to SOC analysts for proactive threat mitigation.
Transformation of Security Operation Center Practices
In an era where cyber threats evolve at an unprecedented pace, the Cybersecurity Operations Center (SOC) stands as the frontline defense against a relentless tide of attacks.
From sophisticated ransomware to AI-driven phishing campaigns, the complexity and scale of modern threats demand a transformation in how SOCs operate. Enter Artificial Intelligence (AI)—a game-changer that is redefining the art and science of cybersecurity:
- Automation of Repetitive Tasks: AI agents like Phishing Triage and Task Optimizer automate high-volume tasks, reducing alert fatigue and freeing analysts for complex investigations. This addresses the cybersecurity talent shortage (4.8 million professionals needed globally) by enabling less experienced analysts to contribute effectively.
- Enhanced Threat Detection and Response: Generative AI sifts through massive datasets to detect patterns, predict breaches, and prioritize critical threats, moving beyond rule-based systems. For example, Security Copilot contextualizes attack signals and recommends remediation, reducing response times.
Automated workflows and scripts streamline incident resolution, minimizing dwell time and improving SOC scalability. - Improved Analyst Productivity and Accuracy: Studies show Security Copilot improves analyst accuracy by 44% and speed by 26%, particularly for “new in career” analysts, by translating threat data into natural language and suggesting actions. Unified platforms reduce tool sprawl, providing a single interface for SIEM, XDR, and posture management, enhancing analyst efficiency.
- Proactive Security Posture Management: AI-driven posture management identifies risks across AI infrastructure, cloud workloads, and identities, enabling SOCs to prevent attacks before they occur.
Continuous monitoring and AI-generated decoys disrupt attack chains early, shifting SOCs from reactive to proactive defense. - Addressing AI-Specific Risks: With 57% of organizations reporting increased security incidents from AI usage, SOCs must secure AI applications. Microsoft’s solutions provide visibility into AI risks (e.g., prompt injections, data leakage) and enforce governance, ensuring compliance with regulations. Multicloud interoperability secures AI across Azure, AWS, and Google Cloud, reducing blind spots for SOCs.
- Collaboration and Threat Intelligence Sharing: AI platforms like Sentinel facilitate public-private partnerships, enabling SOCs to share threat intelligence and standardize processes. This collective defense approach enhances resilience against state-sponsored and financially motivated actors.
Microsoft’s global threat intelligence, processing 84 trillion signals daily, empowers SOCs with unparalleled insights into emerging threats.
Conclusion
Microsoft’s integration of generative AI into its cybersecurity products—through Security Copilot, Defender, Sentinel, Purview, Entra, and unified platforms—revolutionizes SOC practices by automating tasks, enhancing threat detection, and enabling proactive defense.
These advancements address the evolving threat landscape, with 7,000 password attacks per second and a 4.8 million professional shortage, by improving analyst productivity, securing AI infrastructure, and fostering collaboration. SOCs are shifting from reactive to predictive operations, with AI-driven insights and automation reducing response times and strengthening multicloud environments. However, successful transformation requires strategic integration, cost considerations for SMBs, and ongoing governance to ensure responsible AI use.



