Steps toward a Zero Trust architecture on AWS
Implement AWS Verified Access (AVA) to provide secure, VPN-less access to non-HTTP(S) resources (e.g., SSH, RDP, databases) using Zero Trust principles, ensuring strict identity verification, least privilege, and continuous monitoring.
 Modern workplaces have evolved beyond traditional network boundaries as they have expanded to hybrid and multicloud environments. Identity has taken center stage for information security teams.
Modern workplaces have evolved beyond traditional network boundaries as they have expanded to hybrid and multicloud environments. Identity has taken center stage for information security teams.
The need for fine-grained, identity-based authorization, flexible identity-aware networks, and the removal of unneeded pathways to data has accelerated the adoption of Zero Trust principles and architecture.
In this session, learn about different architecture patterns and security mechanisms available from AWS that you can apply to secure standard, sensitive, and privileged access to your critical data and workloads.
Verified Access
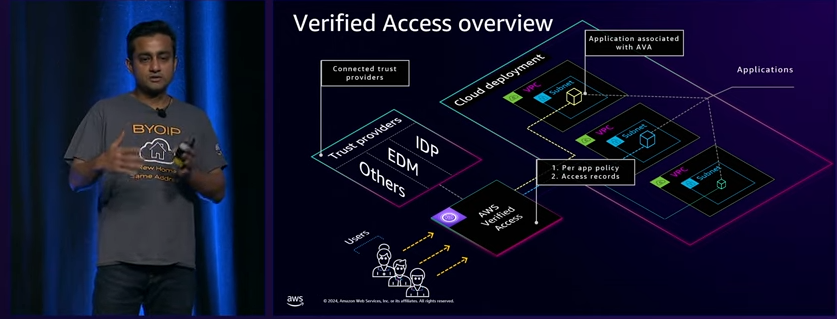
AWS Verified Access (AVA) is a Zero Trust security service that provides secure, VPN-less access to applications and resources, supporting both HTTP(S) and non-HTTP(S) protocols like SSH, RDP, and database connections.
It enforces strict identity verification, device posture checks, and granular access policies to ensure least privilege.
Integrated with identity providers (e.g., AWS IAM Identity Center, Okta) and device management tools (e.g., CrowdStrike), AVA validates users and devices before granting access.
Deployed in a private VPC, it replaces traditional VPNs and bastion hosts, simplifying secure access to resources like EC2 instances or RDS databases. Centralized policy management, continuous monitoring via Amazon CloudWatch, and TLS certificate support enhance security and scalability. AVA offers free initial connections per endpoint, making it cost-effective for organizations seeking to implement Zero Trust architectures.
Key Best Practices
- Strong Authentication: Enforce multi-factor authentication (MFA) via an identity provider (e.g., AWS IAM Identity Center, Okta) to verify user identities.
- Device Posture Checks: Validate device compliance (e.g., security patches, endpoint protection) using tools like CrowdStrike or Jamf before granting access.
- Granular Policies: Create context-aware access policies based on user roles, device status, and resource needs to enforce least privilege.
- Centralized Management: Use AVA’s single interface to manage policies for both HTTP(S) and non-HTTP(S) resources, reducing complexity.
- Eliminate VPNs: Replace VPNs and bastion hosts with AVA for direct, secure access to resources like EC2 instances or RDS databases.
- Continuous Monitoring: Log all access attempts with Amazon CloudWatch or tools like Splunk for real-time anomaly detection and audits.
- Secure Network Setup: Deploy AVA in a private VPC, restrict traffic to AVA’s CIDR range, and use AWS Certificate Manager for TLS certificates.
- Start Small: Pilot AVA with a specific use case (e.g., SSH to EC2) to validate configurations before scaling.
- Educate Teams: Train employees on Zero Trust and AVA usage to foster a security-conscious culture.
Leverage AWS Resources: Use AWS documentation and support for guidance on setup and optimization.
Recommendation: Begin with a pilot for a low-risk non-HTTP(S) workload, such as SSH access to EC2 instances, and expand iteratively. Align AVA deployment with organizational security goals to achieve a robust Zero Trust architecture.



